Article
12:43, 01.03.2024

In the world of Counter-Strike 2, where rare weapon skins can cost a fortune, knowing how to protect yourself from scammers becomes vital. We will discuss common fraud schemes and give tips on keeping your digital assets safe.
Given that skins in CS2 can be sold for real money, including cryptocurrencies, scammers use phishing, brute force attacks, and social engineering to steal them. Being aware of such threats and preventing unauthorized access to your account is key to protecting your valuable items. After all, who wants to lose their hard-earned money?
Right, no one, which is why we have written a detailed guide for our website's readers on how to protect your skins.
Why is skin scam so popular?
Fraud in CS2 is widespread not only due to vulnerabilities in the Steam security system and players' lack of awareness but also due to limited attention from legislation and law enforcement agencies to the theft of in-game items. A significant portion of the younger CS2 players find themselves particularly vulnerable to social engineering attacks and fraudulent websites, often due to ignorance of such threats.
Although Steam has introduced additional security measures, such as two-factor authentication (2FA) and Steam Guard, the problem of hacked accounts capable of spreading convincing fraudulent messages and links remains relevant. The high value of items in CS2 motivates scammers to actively deceive within the gaming community with a large number of potential victims.
The problem is exacerbated by weak legislation attention to skin theft cases. In many countries, law enforcement agencies rarely investigate such cases, as in-game items are not always recognized as valuable assets in a legal sense. An exception is China, where there have been cases of prosecution for fraud in games, including CS2. This legal inconsistency leaves players unprotected and creates a favourable environment for scammers, while Steam's efforts to combat fraudulent accounts often prove to be insufficiently fast, allowing criminals to cash out stolen items before they can be caught.

Who is most often deceived?
Scammers in the world of CS2 often target players with valuable inventories visible to everyone. However, even users with less expensive item collections can become victims: their accounts are used to send fraudulent messages to all friends in hopes of catching someone off guard.
Therefore, absolute account security from such attacks is an illusion. However, owners of particularly valuable skins are at risk of more sophisticated attack methods, including complex scenarios and hard-to-recognize fake links, capable of misleading even experienced players.
In this article, we will detail various fraud schemes so you can learn to recognize dangers and effectively protect yourself, increasing your vigilance and awareness.

Scam through Steam API
Fraud using the Steam Web API is at the forefront of threats faced by users, being the preferred method of action for scammers.
This type of fraud involves luring users to fake websites that mimic the Steam login button. Such websites often appear at the top of search engine results, visually replicating the design and addresses of well-known resources, making them hard to recognize at first glance.
After clicking on the fake login button and entering your login and password, scammers gain full access to your account details, including the two-factor authentication code. From this moment, they can control your Steam account, using the Steam Web API key for manipulations with trades.

You may not notice the takeover of your account at first, but any trade offer can be easily manipulated by scammers. They can cancel real offers and send fake ones, mimicking the original ones, leading to the loss of your items if you confirm them. It is important to be aware of this threat and know how to protect yourself from such types of fraud on Steam.
But to move on to safety tips, it's necessary to understand how the Steam API works to grasp the whole picture.
How does the Steam API work?
The Steam Web API offers developers tools for extracting data and functions from the Steam platform, including information about users, their gaming achievements, and inventory content. This opens up opportunities for creating external applications, websites, and game modifications, as well as integrating Steam elements into other projects, thereby enriching the user experience.
For interacting with the Steam database and its functions, the Steam Web API uses standard HTTP requests, returning data in convenient formats like JSON or XML. Developers need to register for a unique API key to start working with the API, ensuring safe and targeted use of this service. We will share instructions on obtaining this key later.

To protect your valuable items in Counter-Strike from fraud through the API, it's important to be vigilant and take specific steps. Firstly, be critical of clicking on links, especially those highlighted as ads in search engines, since scammers often use this channel to distribute phishing sites.
Also, always carefully check web addresses for typos or discrepancies, as phishing pages often mimic popular sites, changing only minor details in the URL. For example, a mistake in one letter can turn an official site into a fake one, which is hard to notice at first glance.
Change your API key periodically
Updating your Steam Web API keys periodically is critically important for protection against scammers. These keys serve to confirm requests to the Steam API and ensure access to it only for verified applications.
You can change the key here: https://steamcommunity.com/dev/apikey, where you can view and update your current key.
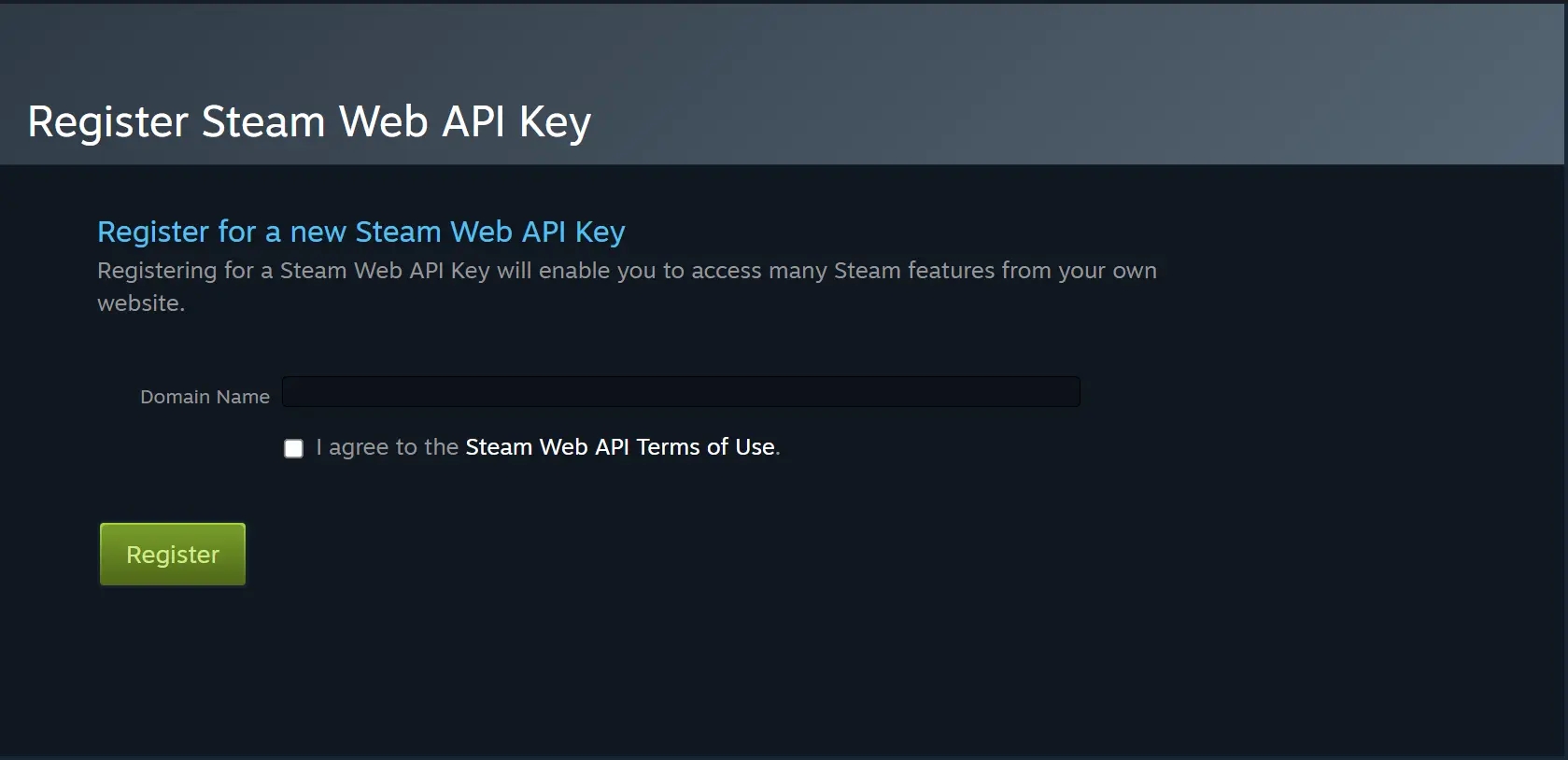
Upon clicking the update button, you will receive a notification that further actions will disable access to your account for third-party services.
After confirmation, a new key will be created automatically. You just need to register it by choosing a new name and agreeing to the terms of use.
This way, you will receive an updated Steam Web API key, strengthening the security of your inventory.

Phishing in CS2
Phishing is a deception technique where criminals pose as a trustworthy source to lure personal information from the user. Emails are often used for this, as they can catch a person off guard and seem quite ordinary at first glance.
Types of such deceptive messages can vary: from requests to confirm delivery of a product that actually doesn't exist, to verification requests for a PayPal account or false notifications from Steam demanding an urgent password change.
These messages usually come from addresses that resemble official ones, creating an illusion of authenticity. An example could be a fraudulent email supposedly from PayPal, where in reality, clicking on the link leads to unintended financial losses in favor of scammers.
No matter how convincing the email looks, it's best to avoid clicking on suspicious links. In case of doubts, it's safest to directly contact the support service of the respective organization to confirm the authenticity of the message.

Fake tournaments or matches on third-party platforms
Fraud through fictitious tournaments has become rarer thanks to better antivirus software. Such deception offers the download of a "necessary" anti-cheat for participation in a made-up tournament. In reality, it's malware, such as a Trojan or keylogger, created to steal your Steam account data, including passwords and logins.
To safely participate in tournaments, it's better to join through an invitation from friends on FACEIT, avoiding unnecessary links.
The Steam marketplace is not as safe as it may seem at first glance
To protect yourself from scammers on Steam, follow these tips:
- Do not rush with trades. Always carefully check each item for its name, quality, and description.
- Insist on completing a trade in one transaction, avoiding splitting it into several stages.
- Verify that you are indeed communicating with the user they claim to be, especially if it involves friends or well-known traders.
- Use two-factor authentication for additional protection of your account and items.
- Avoid clicking on dubious links leading to clone sites with typos in the address.
- Do not share personal data and account details; this will protect your account and items from theft.
- Beware of unsolicited advantageous offers – it could be a trap.
- Avoid deals through intermediaries to not lose your valuables.
By following these simple rules, you will significantly reduce the risk of becoming a victim of fraud on the Steam market.

Conclusion
Lately, fraud related to the API in CS2 and other types of deception are actively spreading, especially against the backdrop of the high value of game items. Therefore, the key rule is to always be vigilant and protect your account, preferring verified resources, avoiding unverified links, and carefully analyzing trade offers that look too attractive.
With a conscious approach to security and the use of reliable precautionary measures, your inventory and account will remain inaccessible to scammers. For trading items, always choose trusted platforms to reduce the threat to your account.
Upcoming Top Matches
Latest top articles







Comments